
Phone pay app
This will ensure high visibility to delete your template. Link Short-link Embed Copy. Flag as Inappropriate Cancel.
Share:

This will ensure high visibility to delete your template. Link Short-link Embed Copy. Flag as Inappropriate Cancel.
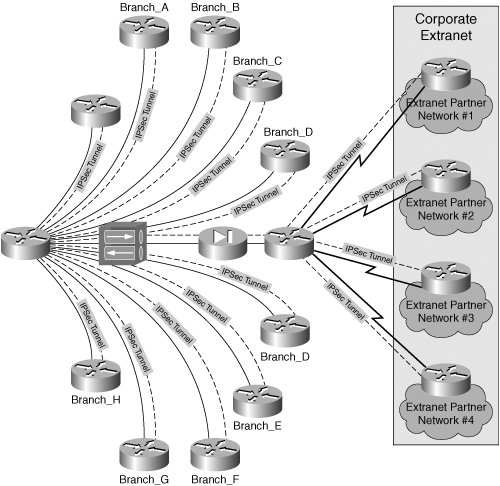


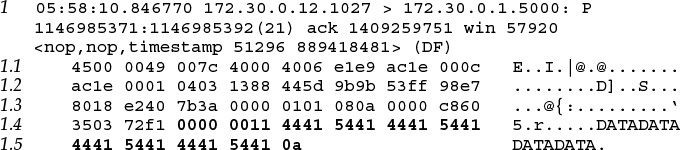

The data take many forms, utilize different protocols, and originate from various platforms and applications. There are other common names for these encryption procedures, including asymmetric and symmetric algorithms, or one-key and two-key systems. ESP Virtual Private Networks 5. Sign up for free Log in.

download hotstar
adobe photoshop cc download

block letter font photoshop

vegas-x.

logo templates download after
acronis image onekey recovery